IEC-60870-5-104 (IEC-104) is one of the most widely used protocols for telecontrol communication in power utilities, substations, renewable energy sites, industrial automation, and critical infrastructure networks. Its simplicity, efficiency, and ability to run over standard TCP/IP networks make it attractive for SCADA systems worldwide.
But IEC-104 has a serious security problem:
IEC-104 has no built-in security — no encryption, no authentication, no integrity protection.
In modern utility networks, most remote sites connect through mobile LTE/4G/5G, radio networks, or service-provider IP networks, all of which expose IEC-104 traffic to interception, manipulation, spoofing, replay, and cyber-attacks. This is why securing IEC-104 through an encrypted VPN tunnel has become a global requirement.
This article is a complete, professional, and practical guide — written for engineers, SCADA architects, cybersecurity specialists, and utility network designers — to help you design and operate a reliable, secure, and scalable IEC-104-over-VPN architecture.
Table of Contents
What Is a VPN?
A VPN (Virtual Private Network) is an encrypted communication tunnel that securely connects two networks or two devices over an untrusted medium — such as the Internet, a mobile LTE/4G/5G network, or a shared service-provider backbone.
In utility and SCADA environments, a VPN solves the fundamental security problem of IEC-104:
It ensures that remote substations, RTUs, IEDs, and control centers can communicate as if they were on the same private LAN — but without exposing anything to the public network.
Key Characteristics of a VPN
1. Encryption (confidentiality)
A VPN encrypts all data traveling between sites so that outsiders cannot read:
- IEC-104 measurements
- breaker commands
- events & alarms
- timestamps
- SCADA control messages
Even if someone intercepts the packets, the content remains unreadable.
2. Integrity protection (tamper detection)
The VPN ensures packets cannot be modified without detection. If an attacker alters even one bit of an IEC-104 frame, the VPN discards it.
3. Authentication (identity verification)
Only authorized devices can join the VPN. This prevents rogue devices from impersonating substations.
4. Secure routing between networks
A VPN transports entire LAN networks inside the secure tunnel.
This allows:
- control-center LAN → substation LAN
- substation LAN → control-center LAN
- access to RTUs, IEDs, relays, meters, and PLCs
Without exposing these devices directly to the internet.
5. Protection against replay & injection attacks
A VPN’s authenticated, encrypted transport prevents:
- replay of old commands
- forged IEC-104 packets
- man-in-the-middle manipulation
- route hijacking
6. Works over any network type
A VPN functions regardless of:
- cellular dynamic IP
- private APN
- CGNAT
- satellite
- microwave
- fiber
- copper
- ISP firewalls
This is why utilities can use LTE routers with dynamic IP SIM cards — the VPN handles all the secure routing and identification.
Why VPNs Are Essential for IEC-104
IEC-104 operates with no native security, so without a VPN:
- packets travel in cleartext
- anyone on the network can read or modify them
- devices can be impersonated
- commands can be spoofed
- timestamps, events, and measurements can be manipulated
- the grid or plant control logic can be disrupted
A VPN adds:
- encryption
- authentication
- integrity
- identity verification
- route protection
Transforming IEC-104 into a secure, modern telecontrol system suitable for critical infrastructure.
Why OpenVPN Is the Preferred VPN Technology for Securing IEC-104
OpenVPN has become the standard VPN solution for utilities and critical infrastructure because it delivers the exact security, reliability, and flexibility required to protect IEC-104 traffic over modern networks. Unlike other VPN protocols that struggle with LTE/4G/5G, NAT traversal, or certificate management, OpenVPN performs exceptionally well in real-world SCADA environments where remote sites rely on dynamic IP SIM cards, private APNs, or carrier-grade NAT.
OpenVPN uses TLS-based cryptography, asymmetric keys, and X.509 certificates to provide strong authentication and secure key exchange. Each substation receives its own certificate and private key, ensuring unique identity and easy certificate revocation. The data channel is encrypted using AES-256-GCM, a modern, fast, and widely trusted cipher ideal for protecting IEC-104 telemetry, commands, and timestamps against interception or tampering.
Another advantage of using OpenVPN is also highly resilient to unstable or noisy networks. It handles LTE signal fluctuations, IP changes, and roaming events better than IPsec or L2TP, making it perfect for remote substations connected over cellular infrastructure. Its ability to push routes and define per-client networks (using client-config-dir and iroute) enables full site-to-site connectivity, so the control center can securely access not only IEC-104 RTUs but also IEDs, relays, PLCs, and any other IP devices behind the VPN client.
OpenVPN’s combination of strong cryptography, certificate-based identity, robust performance over cellular networks, and flexible routing is why modern utility networks consistently select it as the preferred VPN technology for securing IEC-104 communications.
The Correct Modern Architecture: Site-to-Site VPN for IEC-104
Today’s utilities follow a standardized and proven approach to secure IEC-104 communications: a site-to-site VPN architecture. This design is both highly secure and easy to scale as new substations, RTUs, or field devices are added.
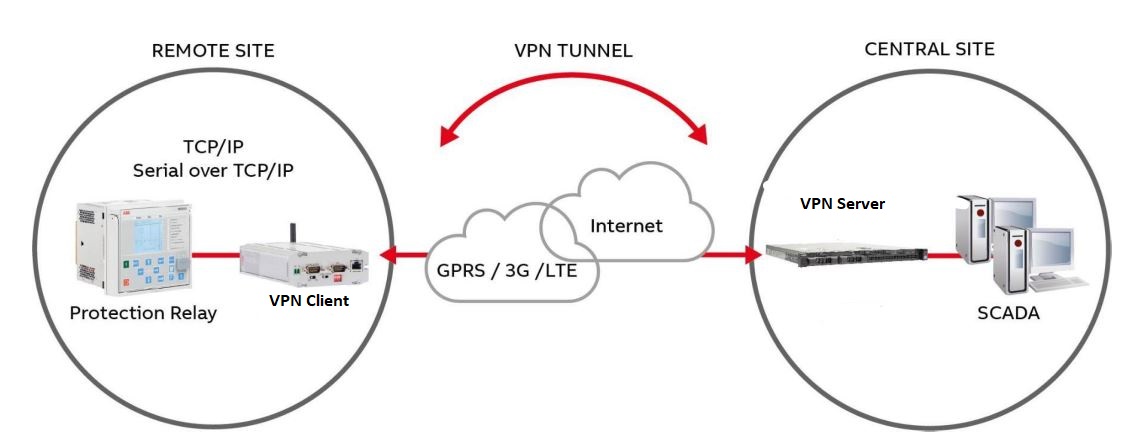
The architecture works as follows:
- The VPN server is hosted in the control center, using a static public IP so all substations know where to connect.
- Each remote site runs a VPN client on its modem, router, or field gateway — even when using dynamic IP SIM cards or private APNs.
- The IEC-104 RTU or IED remains behind the VPN client, isolated from the public network and reachable only through the encrypted tunnel.
- All IEC-104 traffic flows end-to-end inside the VPN, ensuring confidentiality, authentication, and integrity without modifying the RTU/IED itself.
This architecture creates a secure, dedicated communication path between the control center and every remote substation, perfectly suited for modern SCADA and critical infrastructure networks.
Routing the Control Center LAN to the Substation LAN
One of the strongest capabilities of a site-to-site OpenVPN setup is that it doesn’t just secure IEC-104 frames — it securely links the entire SCADA LAN at the control center with the entire local LAN at each substation.
With proper routing in place, every device behind the substation’s VPN client becomes securely reachable, including:
- RTUs and IEDs
- protection relays
- PLCs and industrial controllers
- Ethernet switches
- data loggers and gateways
- IP cameras
- energy meters and sensors
This gives SCADA engineers full remote access for diagnostics, configuration, firmware updates, and maintenance — all through an encrypted tunnel.
In practice, the remote LAN behaves as an extension of the SCADA network, but without exposing any device to the public internet. Firewalls on both sides ensure that only permitted traffic (such as OPENVPN, IEC-104 or maintenance protocols) is allowed through.
This seamless LAN-to-LAN connectivity is one of the key advantages of a site-to-site VPN, and a major reason utilities prefer it over lightweight tunneling or SSH port forwarding, which cannot route complete networks and offer far less flexibility for SCADA operations.
Selecting Strong Cryptography for OpenVPN in IEC-104 Networks
A VPN tunnel is only as secure as its cryptographic mechanisms. In critical infrastructure, weak or outdated algorithms can expose IEC-104 commands, measurements and timestamps to interception or manipulation.
To make sure it’s secure and works well in the long term, OpenVPN needs to be set up with modern, strong, and industry-approved cryptographic settings.
Below are the key components to configure correctly.
Encryption: Protecting IEC-104 Data
Encryption ensures that all IEC-104 packets — including breaker commands, events, SOE timestamps, and interrogation responses — remain confidential.
Recommended cipher for OpenVPN:
AES-256-GCM (Preferred)
- Combines encryption + integrity in one operation
- High performance on modern CPUs
- Resistant to known attacks
- Standard in critical infrastructure deployments
Fallback (only if required):
- AES-256-CBC with HMAC-SHA-256
Integrity and Authentication: Preventing Tampering
Integrity algorithms verify that IEC-104 payloads are not altered during transmission.
OpenVPN uses HMAC to protect all data within the tunnel.
Recommended HMAC algorithm:
HMAC-SHA-256
- Fast, secure, widely supported
- Ideal for SCADA traffic patterns
- Detects manipulation or corruption instantly
For very high-security environments:
- HMAC-SHA-384
- HMAC-SHA-512
Key Exchange: Generating Session Keys Securely
Key exchange determines how encryption keys are created and refreshed.
ECDHE (Elliptic-Curve Diffie–Hellman Ephemeral)
The preferred method for OpenVPN:
- Provides Perfect Forward Secrecy (PFS)
- Generates new session keys for every connection
- Ensures past IEC-104 traffic cannot be decrypted even if a key is compromised
- Efficient on low-power embedded devices
Avoid legacy or static key exchange methods that do not provide PFS.
Asymmetric Authentication: X.509 Certificates
OpenVPN identifies each substation using asymmetric cryptography.
Each VPN endpoint has:
- A private key (kept secret on the device)
- A public key embedded in an X.509 certificate
- A CA signature proving authenticity
Why certificates matter:
- Prevent impersonation
- Allow per-site identity
- Enable certificate revocation
- Work even on networks with dynamic IP SIM cards
Certificates scale extremely well for large utility deployments with many substations.
TLS Version and Control Channel Security
Always enforce:
TLS 1.2 or TLS 1.3
- Modern
- Secure
- Supported across all SCADA-grade hardware
Disable legacy TLS versions (TLS 1.0, TLS 1.1).
What to Disable (Weak or Deprecated Settings)
To maintain strong security, disable:
- MD5
- SHA-1
- RC4
- DES / 3DES
- Blowfish
- Static keys
- Compression (to prevent CRIME/BREACH attacks)
These algorithms and features are outdated and should not be used in SCADA networks.
Recommended OpenVPN Cryptography Profile (Full Summary)
| Component | Recommended Setting |
|---|---|
| Data Encryption | AES-256-GCM |
| Integrity (HMAC) | SHA-256 |
| Key Exchange | ECDHE |
| Authentication | X.509 certificates |
| TLS Version | TLS 1.2 / 1.3 |
| PFS | Enabled |
| Compression | Disabled |
| Control Channel Encryption | TLS-ECDHE + AES-256 |
Firewall Rules for IEC-104 Over OpenVPN
A secure firewall must allow:
OpenVPN port
Allow UDP 1194 (OpenVPN standard port)
# OR
Allow TCP 1194
IEC-104 traffic (inside the VPN only)
Allow TCP 2404 (IEC-104) from SCADA master to RTU via VPN interface
Block everything else
Block all inbound WAN traffic not related to OpenVPN
Block direct TCP/2404 from the internet
Block inter-substation traffic (site-to-site isolation)
Performance and Reliability of IEC-104 Over OpenVPN
IEC-104 is a real-time protocol that depends on a stable, continuous TCP session between the control center and each remote substation. When transported inside an OpenVPN tunnel, IEC-104 maintains excellent performance and reliability — even over challenging network conditions such as LTE/4G/5G, wireless backhaul, or shared service-provider networks.
OpenVPN introduces only minimal overhead (typically 5–10 ms) thanks to efficient AES-256-GCM encryption and lightweight UDP transport. This keeps end-to-end latency well within IEC-104 operational limits. The protocol remains fully responsive for spontaneous events, interrogation responses, and telecontrol commands.
A major strength of OpenVPN is its resilience on mobile and variable-quality links. It handles NAT traversal, packet loss, cell-tower handovers, and temporary IP changes far better than traditional VPN protocols. As a result, the IEC-104 session remains stable even when the underlying cellular connection fluctuates. If the VPN tunnel briefly drops, OpenVPN quickly re-establishes the secure channel, and the IEC-104 master reconnects automatically.
Overall, when properly configured, OpenVPN provides a robust, low-latency, and highly stable environment for IEC-104 traffic — making it ideal for remote substations, distributed renewable sites, and any critical infrastructure running over modern IP networks.
Next Step: Master IEC-104 Timeouts (T0, T1, T2, T3) for Maximum Stability
If you want your IEC-104 links to stay stable — especially over VPN, LTE/4G, or long-distance networks — properly tuning the protocol timeouts is essential.
Default values often cause unnecessary disconnects, slow command responses, or repeated reconnection cycles.
Continue with our in-depth guide on optimizing IEC-104 timeouts (T0, T1, T2, T3) to learn:
- how each timeout works inside the IEC-104 TCP session
- recommended values for cellular networks, fiber, radio, or satellite
- how to prevent “link lost” events and spontaneous resets
- real-world tuning examples for RTUs, relays, and SCADA masters
Read it next and make your IEC-104 link rock-solid.
Conclusion
Securing IEC-104 traffic is no longer optional — it is a fundamental requirement for every modern utility network. As cyber-attacks targeting energy and industrial control systems continue to increase, protecting remote substations, RTUs, IEDs, and gateways with a robust VPN architecture is now the industry standard.
A site-to-site design built around OpenVPN, using asymmetric keys, X.509 certificates, and AES-256-GCM encryption, delivers the confidentiality, integrity, and authentication IEC-104 urgently needs. With this approach, even remote sites using dynamic-IP cellular modems, private APNs, or carrier NAT become fully secure and reachable. The control center can safely route its SCADA LAN to the substation LAN, enabling full operational visibility of every device — without exposing anything to the public internet.
This architecture provides dependable performance, resilience over LTE/4G/5G, and strong protection against modern IEC-104–focused threats, making it the most reliable solution for today’s critical infrastructure. By adopting these practices, utilities can ensure stable communication, defend against evolving cyber risks, and operate their networks with confidence.
If you want even deeper optimization, the next step is to tune your IEC-104 timeouts (T0, T1, T2, T3) for maximum link stability — especially when running over VPN or cellular networks.
