IEC 60870-5-104 (IEC-104) is one of the most widely used telecontrol protocols in electrical power systems. It plays a central role in communication between substations, RTUs, and control centers, especially in transmission and distribution SCADA systems. IEC-104 is reliable, efficient, and well understood by utilities worldwide. However, when the protocol was originally designed, cybersecurity was not a primary concern.
As power system communication evolved from isolated serial lines to interconnected IP networks, the security limitations of IEC-104 became increasingly evident. Modern SCADA systems now operate over Ethernet, routed WANs, optical fiber, VPNs, and sometimes shared telecommunications infrastructure. In such environments, unsecured communication represents a serious risk.
To address this challenge, the IEC introduced IEC/TS 60870-5-7, a technical specification that defines security extensions for IEC 60870-5-101 and IEC 60870-5-104, applying the security principles defined in IEC 62351. This specification provides a standardized and interoperable way to secure IEC-104 communication without changing the protocol’s core behavior.
This article explains the IEC-104 security architecture according to IEC/TS 60870-5-7, covering its motivation, structure, operation, and real-world implementation.
Table of Contents
Why IEC-104 Needs Security
IEC-104 was originally designed for environments where communication networks were considered trusted. Typical assumptions included physical isolation, private ownership of communication links, and limited external connectivity. Under these conditions, the protocol did not require encryption or authentication.
Today, these assumptions are no longer valid. IEC-104 traffic often traverses:
- Wide-area IP networks
- Utility backbone networks shared by multiple services
- VPN tunnels over public infrastructure
- Routed and segmented OT networks
Without security, IEC-104 communication is exposed to several threats. Attackers could intercept traffic and read operational data, modify messages in transit, replay valid commands, or impersonate a control center or substation. Because IEC-104 includes control commands, such attacks can have serious operational and safety consequences.
IEC/TS 60870-5-7 was developed specifically to mitigate these risks while preserving interoperability and backward compatibility.
Purpose and Scope of IEC/TS 60870-5-7
IEC/TS 60870-5-7 is a security extension, not a replacement for IEC-104. Its purpose is not to redesign the protocol, but to secure its transmission.
The specification aims to:
- Protect IEC-104 communication against unauthorized access
- Ensure confidentiality and integrity of data
- Authenticate communication partners
- Prevent replay and tampering attacks
- Maintain compatibility with existing IEC-104 systems
A key design principle is that IEC-104 itself remains unchanged. ASDUs, frame formats, causes of transmission, addressing, and timing behavior are exactly the same as in unsecured IEC-104. Security is added below the application layer.
High-Level Security Architecture
The fundamental architectural concept in IEC/TS 60870-5-7 is the use of Transport Layer Security (TLS) to protect IEC-104 communication.
In unsecured IEC-104, the protocol stack is:
IEC-104 TCP IP Ethernet
According to IEC/TS 60870-5-7, security is introduced as follows:
IEC-104 TLS TCP IP Ethernet
This means that all IEC-104 messages are transported inside a secure TLS tunnel. TLS provides encryption, integrity protection, authentication, and replay protection, while TCP continues to handle reliable data delivery.
From the perspective of the IEC-104 application layer, nothing changes. The protocol behaves exactly as before, but the underlying transport is now secure.
TLS as the Foundation of IEC-104 Security
IEC/TS 60870-5-7 relies on TLS as the primary security mechanism. TLS is a widely adopted and well-tested security protocol used in many critical applications, including web communication and industrial control systems.
TLS provides several essential security properties:
- Confidentiality through encryption
- Integrity through cryptographic checks
- Authentication using certificates
- Replay protection through session management
By adopting TLS, IEC-104 security benefits from proven cryptographic mechanisms and existing implementation experience.
Secure Connection Establishment
1. TCP Connection Setup
The secured IEC-104 communication process begins with a standard TCP connection. The controlled station (server) listens on a secure IEC-104 port, and the controlling station (client) initiates the connection.
IEC/TS 60870-5-7 defines TCP port 19998 as the default port for secured IEC-104 communication. This port is configurable, but the default value ensures interoperability across vendors.
This design clearly separates secured and unsecured communication:
- TCP port 2404 → unsecured IEC-104
- TCP port 19998 → secured IEC-104
2. TLS Handshake
Immediately after the TCP connection is established, a TLS handshake takes place. This step is critical, as it establishes trust and security before any IEC-104 data is exchanged.
During the TLS handshake:
- Cryptographic algorithms are negotiated
- Encryption parameters are agreed upon
- Certificates are exchanged
- Both endpoints authenticate each other
IEC/TS 60870-5-7 requires mutual authentication, meaning that both the client and the server must prove their identity. This prevents unauthorized devices from connecting to the SCADA system.
If authentication fails at any stage, the connection is terminated.
3. Secure Channel Established
Once the TLS handshake completes successfully, a secure encrypted channel is established. All subsequent communication is protected by TLS.
Only after this secure channel exists does IEC-104 communication begin.
IEC-104 Session Inside the Secure Channel
Once the TLS handshake has been successfully completed, a secure communication channel is established between the controlling station and the controlled station. From this point onward, all IEC-104 traffic is encrypted, integrity-protected, and authenticated at the transport layer. Only after this secure channel exists does the IEC-104 protocol itself begin operation.
Inside the TLS tunnel, IEC-104 behaves exactly as defined in the base standard. The session startup follows the normal sequence using STARTDT act and STARTDT con, after which data transfer is enabled. Information frames (I-frames) carry ASDUs, supervisory frames (S-frames) handle acknowledgments, and unnumbered frames (U-frames) manage session control. From a protocol perspective, there is no difference between secured and unsecured IEC-104 operation at this level.
However, when application-layer security according to IEC 62351-5 is enabled—as allowed and referenced by IEC/TS 60870-5-7—additional security-related message exchanges occur inside the already established TLS tunnel. These exchanges provide enhanced authentication, session key management, and message integrity, adding a second layer of protection on top of TLS.
The figure below illustrates this combined behavior, showing how standard IEC-104 communication is interleaved with security-specific exchanges. The diagram highlights the coexistence of normal IEC-104 message flow and security mechanisms such as key status checks, session key changes, and challenge–response authentication.
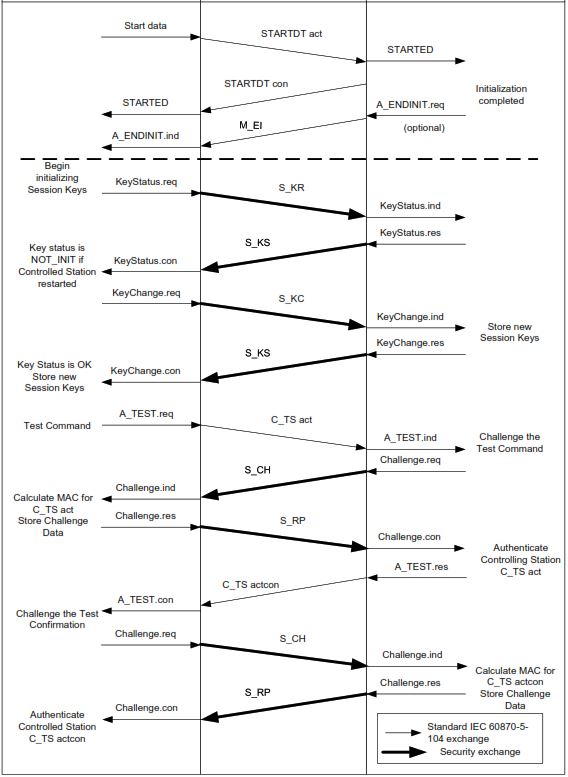
After the IEC-104 session is started, the communicating devices may initiate session key initialization or verification. This includes exchanging key status information to confirm whether valid session keys already exist or whether new keys must be generated. If keys are missing, outdated, or invalid, a controlled key change procedure is executed. New session keys are generated, exchanged securely, and stored by both parties without interrupting the IEC-104 session.
To authenticate critical operations and verify the identity of the controlling station, a challenge–response mechanism may be triggered. As shown in the figure, a test command is issued, followed by a cryptographic challenge. The responding device calculates a message authentication code (MAC) using the current session keys and returns it for verification. Successful validation confirms that the sender is legitimate and that the session has not been compromised.
Throughout this process, normal IEC-104 communication continues. Measurements, indications, commands, and acknowledgments are exchanged as usual, while security-related messages operate in parallel. This design ensures that enhanced security does not disrupt real-time SCADA behavior.
It is important to emphasize that this figure does not represent the TLS handshake. TLS has already been established before any of these exchanges occur. Instead, the diagram represents application-layer security mechanisms operating inside the secure transport channel, providing defense-in-depth as defined by IEC/TS 60870-5-7 and IEC 62351-5.
In summary, the IEC-104 session inside the secure channel consists of three tightly integrated layers:
TLS provides encrypted and authenticated transport, IEC-104 handles telecontrol communication, and optional application-layer security mechanisms manage session keys and authenticate critical actions. Together, these layers form a robust and interoperable security architecture suitable for modern SCADA systems.
What the Security Architecture Protects
The IEC-104 security architecture defined by IEC/TS 60870-5-7 provides protection in several dimensions.
Confidentiality
All IEC-104 data is encrypted. Unauthorized parties cannot read measurements, statuses, or control commands.
Integrity
Any modification of data during transmission is detected. Altered messages are rejected.
Authentication
Both communication partners are verified. Only trusted control centers and substations can communicate.
Replay Protection
Captured messages cannot be resent to trigger unauthorized actions.
Importantly, this protection does not alter IEC-104 semantics. The meaning of data remains unchanged.
Certificates and Trust Model
IEC/TS 60870-5-7 uses a certificate-based trust model, typically based on X.509 certificates.
In practice:
- Each IEC-104 endpoint has its own certificate
- Certificates are issued by a trusted authority
- Private keys are securely stored in the device
- Certificate validity is checked during connection setup
This approach ensures strong identity verification and scalable trust management across large SCADA systems.
Port Separation and Migration Strategy
One of the practical strengths of IEC/TS 60870-5-7 is the separation between secured and unsecured communication using different TCP ports.
This allows utilities to:
- Run secured and unsecured IEC-104 in parallel
- Gradually migrate legacy systems
- Apply clear firewall and network rules
- Monitor encrypted and unencrypted traffic separately
During migration, a control center may support both port 2404 and port 19998, allowing older RTUs to coexist with newer, secured devices.
Application-Layer Security and IEC 62351-5
While TLS provides transport-level security, IEC/TS 60870-5-7 also supports optional application-layer security mechanisms defined in IEC 62351-5.
These mechanisms add:
- Message authentication codes (MACs)
- Additional replay protection
- Secure key management
Application-layer security operates inside the TLS tunnel, providing defense-in-depth. Vendors may implement TLS alone or TLS combined with IEC 62351-5, depending on security requirements.
Real-World Implementation Example
In real devices such as modern RTUs and gateways, IEC-104 security configuration typically includes:
- Enabling TLS for IEC-104 lines
- Selecting certificates for authentication
- Configuring allowed cipher suites
- Enforcing minimum key lengths
- Choosing secure TCP ports
- Optionally enabling IEC 62351-5 authentication
This layered configuration reflects the architecture defined in IEC/TS 60870-5-7 and demonstrates that the specification is practical and implementable.
Operational Impact on SCADA Systems
From an operational point of view, the impact of IEC-104 security is manageable.
What stays the same:
- IEC-104 addressing
- ASDUs and data models
- Polling and spontaneous reporting
- Control command handling
What changes:
- Certificate and key management
- Security monitoring
- Network and firewall configuration
Latency increases slightly due to encryption, but this is usually negligible in modern networks.
Relationship to IEC 62351
IEC/TS 60870-5-7 applies the general cybersecurity framework defined in IEC 62351 to the IEC-60870-5 protocol family.
In simple terms:
- IEC 62351 defines security concepts and requirements
- IEC/TS 60870-5-7 applies those concepts specifically to IEC-104
Together, they form a consistent and standardized approach to securing power system communication.
Conclusion
IEC/TS 60870-5-7 provides a clear, practical, and interoperable security architecture for IEC-104. By introducing TLS between the protocol and the TCP/IP transport layer, it secures communication without changing IEC-104 behavior or data structures.
This approach allows utilities to protect their SCADA networks against modern cyber threats while preserving compatibility with existing systems. The separation of secured and unsecured communication, support for mutual authentication, and optional application-layer security make IEC/TS 60870-5-7 a robust foundation for secure IEC-104 deployments.
As power systems continue to evolve toward IP-based and interconnected architectures, IEC/TS 60870-5-7 plays a critical role in ensuring that IEC-104 remains a trusted and secure protocol for the future.
