IACS Cybersecurity focuses on protecting Industrial Automation and Control Systems (IACS) such as SCADA, PLCs, RTUs, DCS, IEDs, and industrial networks from cyber threats while ensuring safety, availability, and operational reliability.
For operators of critical infrastructure—power utilities, oil and gas, manufacturing, water, and renewable energy—cybersecurity is no longer optional. Modern industrial systems are connected, remote-access enabled, and increasingly targeted by cyberattacks.
Table of Contents
What Is IACS Cybersecurity?
IACS Cybersecurity is the application of security policies, technologies, and procedures specifically designed for operational technology (OT) environments.
Unlike IT systems, industrial control systems:
- Operate in real time
- Control physical processes
- Often run 24/7
- Use legacy protocols not designed with security in mind
Because of this, traditional IT security approaches cannot be directly applied to SCADA and control systems.
Why IACS Cybersecurity Is Critical
Cyber incidents in industrial environments can cause:
- Process shutdowns
- Equipment damage
- Safety risks to people
- Environmental impact
- Long recovery times
Threats include:
- Malware and ransomware
- Unauthorized remote access
- Insider threats
- Supply chain vulnerabilities
- Misconfigured networks and devices
IACS cybersecurity is about risk reduction, not just compliance.
IACS Cybersecurity vs IT Cybersecurity
| IT Cybersecurity | IACS Cybersecurity |
|---|---|
| Focus on data confidentiality | Focus on safety and availability |
| Frequent patching | Risk-based patching |
| Short system lifecycle | 15–30 year lifecycle |
| Downtime acceptable | Downtime often unacceptable |
| Standard protocols | Proprietary & legacy protocols |
This difference is why dedicated OT security strategies are required.
Core Principles of IACS Cybersecurity
Defense in Depth
Multiple layers of security are used so that if one control fails, others remain in place.
Risk-Based Approach
Security controls are selected based on risk, not checkbox compliance.
Least Privilege
Users and systems only receive the access they absolutely need.
Segmentation
Industrial networks are divided into zones and conduits to limit attack spread.
Key Components of an IACS Cybersecurity Program
Asset Inventory
You cannot protect what you do not know.
- Controllers, servers, workstations
- Network devices and gateways
- Firmware, software, and versions
Network Segmentation & Architecture
- Separation of IT and OT networks
- Industrial DMZs
- Firewalls between security zones
- Controlled conduits for data flow
Secure Remote Access
- VPN-based remote access
- Jump servers / bastion hosts
- Multi-factor authentication
- Session logging and monitoring
System Hardening
- Disable unused services and ports
- Secure configurations for PLCs and servers
- Remove default passwords
- Restrict protocol usage
Patch & Vulnerability Management
- Vendor-approved patching
- Testing before deployment
- Compensating controls when patching is not possible
- Clear patching policies
Monitoring & Detection
- Network traffic monitoring
- Anomaly detection
- Log collection and analysis
- Alerting for suspicious behavior
Backup & Recovery
- Regular backups of:
- SCADA servers
- PLC logic
- Network configurations
- Offline and immutable backups
- Tested recovery procedures
IACS Cybersecurity Lifecycle
A strong cybersecurity program follows a continuous lifecycle:
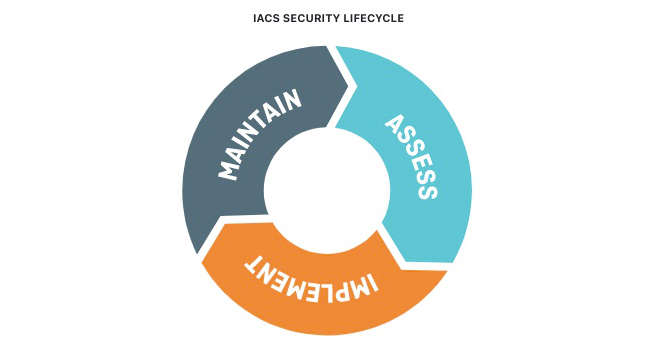
- Assess
- Identify systems and risks
- Define security zones
- Set target security levels
- Implement
- Apply technical and procedural controls
- Configure networks and devices securely
- Validate security through testing
- Maintain
- Monitor systems
- Manage vulnerabilities
- Respond to incidents
- Perform regular audits
Cybersecurity is not a one-time project—it is an ongoing operational responsibility.
Standards and Best Practices
IACS cybersecurity is commonly aligned with:
- ISA/IEC 62443 series
- NIST SP 800-82
- NIST Cybersecurity Framework (CSF)
These frameworks provide guidance for asset owners, system integrators, and vendors across the full system lifecycle.
Typical IACS Cybersecurity Use Cases
- SCADA network protection
- Substation cybersecurity
- Secure remote access for field engineers
- Legacy system modernization
- Compliance-driven security programs
- Incident response planning
Who Needs IACS Cybersecurity?
- Power generation, transmission, and distribution
- Oil and gas facilities
- Manufacturing plants
- Water and wastewater utilities
- Renewable energy sites
- Any organization operating SCADA or industrial control systems
Conclusion
IACS Cybersecurity is essential for protecting modern industrial operations against evolving cyber threats. By combining risk-based security, network segmentation, system hardening, and continuous monitoring, organizations can significantly reduce cyber risk without compromising operational reliability.
As industrial systems become more connected, cybersecurity must be treated as a core engineering discipline, not an afterthought.
