In modern SCADA (Supervisory Control and Data Acquisition) systems, choosing the right communication protocol can determine how efficiently, securely, and reliably data moves between control centers and field equipment.
Two of the most widely used open standards are DNP3 (Distributed Network Protocol version 3) and IEC 60870-5-104.
While both were designed for real-time monitoring and control, they differ in architecture, transport mechanisms, data handling, and security design.
This article compares both protocols in depth to help determine which is better suited for specific SCADA applications.
Table of Contents
Protocol Overview
| Protocol | Full Name | Primary Standard | Primary Use |
|---|---|---|---|
| DNP3 | Distributed Network Protocol v3 | IEEE 1815-2020 | North American SCADA systems, substations, and utilities |
| IEC 60870-5-104 | IEC Telecontrol Protocol (TCP/IP version) | IEC 60870-5-104 | European and international power transmission systems |
Both are open, interoperable protocols designed for communication between a control center (master) and remote terminal units (RTUs) or intelligent electronic devices (IEDs).
Their common goal: reliable, deterministic, and time-stamped data exchange over unreliable networks
Design Philosophy and Origins
DNP3 (IEEE 1815)
- Developed in the early 1990s by Harris Controls (GE).
- Derived from IEC 60870-5-101 concepts but independently extended for reliability.
- Focuses on event-driven reporting, time tagging, and error tolerance for long-distance, noisy channels.
- Widely used in North America, Australia, and critical infrastructure networks (electric, water, gas).
IEC 60870-5-104
- Developed by the International Electrotechnical Commission (IEC) as part of the 60870-5 family.
- Extends the serial-based IEC 101 into the TCP/IP world (port 2404).
- Follows a continuous polling and cyclic data exchange philosophy.
- Commonly deployed across Europe, Asia, and transmission-level systems.
Layer Architecture Comparison
Both DNP3 and IEC 60870-5-104 are structured using simplified subsets of the OSI model, optimized for industrial automation rather than general-purpose networking.
However, they differ in how they map communication functions across these layers.
DNP3 (Enhanced Performance Architecture – EPA)
Default Port: 20000 (TCP/UDP)
DNP3 uses a three-layer “Enhanced Performance Architecture” (EPA) derived from the OSI model.
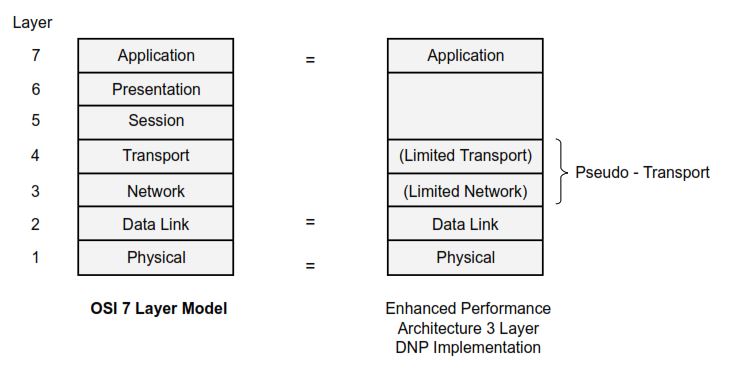
This structure was designed for deterministic behavior, error recovery, and interoperability across unreliable communication links such as serial, radio, or IP-based networks.
Layer Breakdown:
| OSI Layer | DNP3 Function | Description |
|---|---|---|
| Application Layer (Layer 7) | SCADA commands, data objects | Handles requests/responses, event reporting, select-before-operate logic, and time-tagged data (SOE). |
| Pseudo-Transport Layer (Layer 4) | Message segmentation and reassembly | Breaks long application messages into 249-byte segments, tracks sequence numbers, and ensures ordered delivery. |
| Data Link Layer (Layer 2) | Frame control, CRC, acknowledgments | Ensures reliable frame delivery with error checking, retry, and primary/secondary addressing. |
| Physical Layer (Layer 1) | RS-232 / RS-485 / Ethernet / Radio | Defines signaling and timing for wired or wireless transmission. |
IEC 60870-5-104
Default Port: 2404 (TCP)
IEC 60870-5-104 extends the legacy IEC 60870-5-101 serial protocol into the TCP/IP domain.
It maps its application service data units (ASDUs) directly over the Internet Protocol suite while relying on TCP for reliable delivery.
Layer Breakdown:
| OSI Layer | IEC 104 Function | Description |
|---|---|---|
| Application Layer (Layer 7) | ASDUs and IOAs (telecontrol messages) | Defines message types (e.g., measured values, commands, status) and transmission causes (COT). |
| Transport Layer (Layer 4) | TCP | Provides connection-oriented delivery, flow control, and retransmission. |
| Network Layer (Layer 3) | IP | Handles addressing and routing for wide-area networks. |
| Data Link Layer (Layer 2) | Ethernet MAC | Frame encapsulation for LAN communication. |
| Physical Layer (Layer 1) | Ethernet / Fiber / Wireless | Physical connectivity for transmission (IEEE 802.3). |
Notable Traits:
- Pure TCP/IP-based—no serial mode in the base IEC 104 specification.
- Uses sequence numbers (send/receive counters) to track acknowledged frames.
- Relies on Cyclic and Spontaneous transmission modes for data updates.
- Optional TLS security via IEC 62351-3 provides encryption and authentication.
IEC 60870-5-104 leverages standard IP networking layers for scalability and simplicity, making it ideal for high-speed control center and transmission-level systems.
Data Handling and Event Reporting
DNP3
DNP3 structures data into objects grouped by type and variation, enabling efficient, event-driven communication. It’s designed for reliable operation over both serial links and IP-based networks using port 20000 (TCP/UDP).
Key characteristics:
- Organizes information as Object Groups and Variations (e.g., Group 1 – Binary Input, Group 10 – Binary Output, Group 30 – Analog Input).
- Operates in Class 0 (static) and Classes 1–3 (event) data modes.
- Class 0 = full data snapshot (poll).
- Class 1–3 = buffered events, prioritized by importance.
- Each event includes a timestamp, quality flags, and a sequence number, supporting precise Sequence of Events (SOE) recording.
- Implements Select-Before-Operate (SBO) to ensure control safety:
- The master first sends a “select” command to verify device readiness.
- The “operate” command executes only if it matches the previous selection, confirmed by acknowledgment and sequence validation.
- Uses report-by-exception and unsolicited responses to send only changed data, conserving bandwidth on large-scale networks.
- Supports event buffering—if communication is lost, events are stored locally and retransmitted when the link is restored.
- Communication can occur via:
- Serial links (RS-232/RS-485)
- Ethernet / TCP/IP or UDP/IP using port 20000
This design makes DNP3 ideal for geographically distributed or low-bandwidth SCADA systems requiring high data integrity and secure event handling.
IEC 104
IEC 60870-5-104 (IEC 104) organizes data into ASDUs (Application Service Data Units) containing one or more Information Objects (IOAs), transmitted over TCP/IP.
Key characteristics:
- Derived from IEC 60870-5-101 but mapped to Ethernet/TCP transport (port 2404).
- Supports several reporting modes defined in IEC 60870-5-5:
- Cyclic data transmission for periodic polling.
- Event acquisition for spontaneous, event-driven updates.
- General interrogation to retrieve complete datasets on demand.
- Implements Select-Before-Operate (SBO) using command types such as C_SC_NA_1 (single command) and C_DC_NA_1 (double command).
- The select phase confirms device availability and parameter validity.
- The operate phase executes only if the select acknowledgment is valid — preventing accidental operations.
- Provides optional cause-of-transmission codes (COT) for status tracking (e.g., activation, spontaneous, acknowledgment).
- Unlike DNP3, IEC 104 does not include event buffering or quality-bit metadata within the base protocol, though these can be added via IEC 62351 extensions.
IEC 104’s ASDU model simplifies implementation for high-speed, IP-based SCADA environments, while maintaining deterministic command control via SBO sequences.
Time Synchronization
DNP3 (IEEE 1815)
DNP3 provides highly accurate millisecond-level time synchronization, making it ideal for Sequence of Events (SOE) recording in substation and distributed control systems.
Time synchronization ensures that every event reported from an RTU or IED carries a consistent and traceable timestamp.
Key characteristics:
- Synchronization method:
The master station periodically sends a Time Synchronization command (Function Code 32) to all outstations.
Each outstation adjusts its local clock to match the master’s time reference. - Precision: Typically within ±1 ms, depending on the network delay and device resolution.
- Timestamp format:
Events carry 48-bit absolute timestamps with millisecond resolution (using UNIX-style epoch reference). - Time source:
The DNP3 master can synchronize from GPS, NTP, or PTP (IEEE 1588) sources, then distribute that time to all outstations via DNP3. - Clock Drift Management:
Outstations may request resynchronization when the local clock deviates beyond configured thresholds.
In short: DNP3’s timestamping is integral to its protocol logic—not an add-on. Every binary input, analog value, and event can carry an SOE timestamp for precise historical reconstruction.
IEC 60870-5-104
IEC 104 offers robust time synchronization but with lower granularity compared to DNP3. It supports centralized clock control from the SCADA master, following the model originally defined in IEC 60870-5-101.
Key characteristics:
- Synchronization method:
Uses the Clock Synchronization command (C_CS_NA_1) — the control center periodically sends this to outstations over port 2404 (TCP). - Precision:
Typically achieves ±10–20 ms, depending on transmission delay and TCP stack behavior. - Timestamp format:
Uses CP56Time2a, a 7-byte timestamp structure with milliseconds and date/time fields, providing up to 1 ms resolution but limited by implementation. - Spontaneous updates:
Devices can send spontaneous time-tagged events (M_SP_TA_1, M_DP_TA_1), though buffering and accuracy depend on device implementation. - Time source:
The master usually references GPS, NTP, or a redundant clock system, distributing synchronization downstream to all substations.
In short: IEC 104 provides reliable, centralized time alignment for transmission-level systems, but its precision and security depend heavily on the underlying TCP/IP infrastructure and IEC 62351 implementation.
Security and Authentication
Cybersecurity is now a defining factor in SCADA protocol design.
Both DNP3 and IEC 60870-5-104 were initially created for trusted, isolated networks,
but modern deployments across IP and public infrastructures demand built-in protection against spoofing, replay, and unauthorized control.
The two protocols take very different approaches to securing communication:
DNP3 integrates security natively, while IEC 104 relies on external standards like IEC 62351 and TLS.
DNP3 (IEEE 1815-2020 – Secure Authentication Version 6, SAv6)
Default Port: 20000 (TCP/UDP)
The IEEE 1815-2020 standard defines Secure Authentication Version 6 (SAv6) —
a protocol-level cybersecurity framework built directly into DNP3.
It adds encryption, authentication, authorization, and key management as part of the DNP3 stack itself, eliminating dependence on external wrappers like VPNs or TLS tunnels.
Key Security Features:
- Authenticated Encryption (AES-256-GCM):
- Provides both data confidentiality and message integrity.
- Protects all SCADA control and monitoring messages.
- Prevents replay and tampering through nonces and message authentication codes (MACs).
- Authorization Management Protocol (AMP):
- Implements Role-Based Access Control (RBAC) and centralized authorization.
- Defines which users, masters, or applications can perform control actions on each outstation.
- Managed by a trusted Authority or Key Management Server (KMS).
- LESS Enrollment (Low-Entropy Shared Secret):
- Simplifies device commissioning by bootstrapping cryptographic keys using a short shared secret.
- Automatically generates Update Keys and Session Keys with AES-256 Key Wrap.
- Session Management:
- Keys rotate periodically, ensuring Perfect Forward Secrecy (PFS).
- Devices can renegotiate sessions automatically after power cycles or network changes.
- Backward Compatibility:
- Devices supporting SAv5 (IEEE 1815-2012) can still communicate securely with SAv6 peers.
- If an outstation is non-secure, communication gracefully reverts to classic DNP3 mode.
- Integrity and Authentication Algorithms:
- HMAC-SHA-256, AES-GMAC, and AES-GCM for message validation.
- All secured communication remains on port 20000, avoiding firewall reconfiguration.
DNP3’s integrated SAv6 security layer makes it a natively secure industrial protocol, capable of protecting against message injection, command spoofing, and replay — without depending on external encryption systems.
IEC 60870-5-104 (with IEC 62351 Security Extensions)
IEC 60870-5-104 was not originally designed with embedded security.
However, the IEC 62351 series defines optional extensions to secure IEC telecontrol protocols, including encryption, authentication, and key management.
Key Security Features:
- IEC 62351-3 – TLS Protection:
- Introduces Transport Layer Security (TLS) over port 2404 or an alternate secure port.
- Provides encryption and server/client authentication via X.509 certificates.
- Protects data against eavesdropping and modification in transit.
- IEC 62351-4 – Secure Authentication for IEC 60870-5:
- Adds digital signatures to ASDU control messages.
- Uses symmetric or asymmetric algorithms (RSA, ECDSA) to verify command authenticity.
- IEC 62351-5 – Key and Certificate Management:
- Defines procedures for certificate issuance, revocation, and renewal.
- Enables integration with Public Key Infrastructure (PKI) systems.
- Security Profiles:
- Utilities can choose between TLS-only (simpler) or full PKI-based authentication (more secure).
- TLS can be terminated at the gateway or end device depending on architecture.
- Operational Security:
- Firewall segmentation and VPN tunnels are still common protective layers.
- Security logging and role management often implemented externally by SCADA systems.
IEC 104 achieves strong protection when paired with IEC 62351 and TLS,
but these mechanisms are add-ons — not part of the base protocol.
Security therefore depends heavily on implementation consistency and certificate management across vendors.
Performance and Scalability
DNP3 (IEEE 1815-2020)
Port: 20000 (TCP/UDP)
DNP3 is engineered for low-bandwidth, high-latency environments—radio, microwave, and serial links—where bandwidth efficiency and data integrity are crucial.
Key performance features:
- Report-by-Exception (RBE): Only transmits changed data, drastically reducing average bandwidth consumption by 70–90 % compared to cyclic protocols.
- Unsolicited Reporting: Outstations can push updates to masters without polling, cutting round-trip latency.
- Segmented Transmission: The pseudo-transport layer fragments large messages into 249-byte frames, ensuring reliable delivery even over noisy links.
- Retry and Confirmation Logic: Built-in ACK/NAK at the data-link layer plus CRC validation provide deterministic recovery from packet loss.
- Latency: Typically 50–100 ms over Ethernet, 150–400 ms over radio networks depending on signal strength.
- Scalability: Addresses up to 65 000+ devices with unique node IDs on a single master link.
Result: DNP3 maintains high efficiency under constrained networks and scales exceptionally well in distributed, event-driven architectures.
IEC 60870-5-104
Port: 2404 (TCP)
IEC 104 is optimized for high-speed, IP-based environments such as transmission grids and control centers, leveraging the TCP stack for reliability.
Key performance features:
- Cyclic and Spontaneous Modes: Cyclic polling is used for steady-state updates; spontaneous ASDUs handle event bursts.
- TCP Sliding Window: Ensures ordered delivery with minimal retransmission delay, ideal for fiber or MPLS networks.
- Frame Efficiency: Single TCP connection carries multiple ASDUs per packet, lowering protocol overhead for large datasets.
- Latency: Typical 10–30 ms on fiber or Ethernet networks; rarely exceeds 100 ms unless routed through VPNs or congested WANs.
- Scalability: Supports hundreds of IEDs per master; practical limits arise from connection state tables rather than addressing.
- Bandwidth Use: Moderate—continuous cyclic traffic even when no data changes.
Result: IEC 104 performs best on reliable, high-bandwidth IP infrastructures, providing predictable timing and straightforward scalability within regional control networks.
Interoperability and Industry Adoption
| Region / Sector | Preferred Protocol | Reason |
|---|---|---|
| North America | DNP3 | Utility standard (IEEE 1815) |
| Europe / Asia | IEC 60870-5-104 | IEC standard and legacy systems |
| Substations | DNP3 | Advanced SOE and SA support |
| Transmission Networks | IEC 104 | Integrated with telecontrol systems |
| Water / Oil / Gas | DNP3 | Long-distance, low-bandwidth resilience |
Use Cases and Recommendations
| Scenario | Recommended Protocol | Rationale |
|---|---|---|
| Substation Automation | DNP3 | High integrity, time tagging, SAv6 security |
| Transmission Control Centers | IEC 104 | Simpler integration, widespread adoption |
| Rural or Radio Networks | DNP3 | Robust over unreliable links |
| High-speed Fiber Networks | IEC 104 | Efficient over TCP/IP backbone |
| Cross-vendor Interoperability | DNP3 | Strong multi-vendor compliance (IEEE 1815) |
| Cybersecure SCADA Systems | DNP3 (SAv6) | AES-256-GCM + AMP RBAC |
Conclusion
Both DNP3 and IEC 60870-5-104 are proven, reliable SCADA communication standards—but their strengths differ by environment.
- Choose DNP3 for distributed, event-driven systems needing timestamped data, high integrity, and built-in encryption.
- Choose IEC 104 for centralized, IP-based networks where simplicity and standard IEC integration matter most.
In the modern SCADA landscape, many systems even bridge both protocols—leveraging IEC 104 for backbone communication and DNP3 for substation-level intelligence.
Ultimately, the best protocol is the one that matches your network’s topology, performance requirements, and security posture.
