Modern SCADA and utility automation systems face growing cybersecurity demands. The Distributed Network Protocol (DNP3)—the backbone of many control networks—has evolved to meet them.
With the release of IEEE 1815-2020, the DNP3 Secure Authentication Version 6 (SAv6) specification brings authenticated encryption, centralized authorization, and simplified key management directly into the protocol.
This article explains how SAv6 improves on previous versions and how it delivers practical, scalable protection for mission-critical infrastructure.
Below is a detailed breakdown of how DNP3 SAv6 enhances security, authorization, and key management across SCADA networks.
Table of Contents
Background: From DNP3-SA (SAv5) to SAv6
Earlier security, defined in IEEE 1815-2012 (SAv5), added message authentication and integrity using HMAC-SHA-256 or AES-GMAC.
While effective against spoofing and replay, it left three major gaps:
- No encryption—traffic remained visible.
- No centralized authorization model.
- Complex manual key enrollment.
SAv6 (IEEE 1815-2020) closes all three gaps. It aligns DNP3 with modern cybersecurity frameworks such as IEC 62443 and NERC CIP, while remaining backward-compatible with earlier implementations.
Simplified Security Architecture
SAv6 defines two complementary protocols that sit between the DNP3 Application Layer and transport functions:
- DNP3 Secure Authentication (SA) – provides encryption, integrity, and replay protection.
- Authorization Management Protocol (AMP) – manages which entities are authorized to communicate and enforce role-based access control (RBAC).
This modular design simplifies deployment and separates security policy (AMP) from message protection (SA).
DNP3 SAv6 Security Architecture Explained
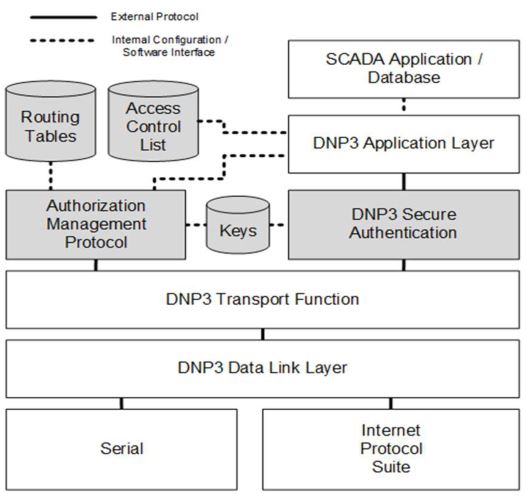
The diagram above illustrates how DNP3 Security Version 6 integrates authentication, authorization, and encryption into the traditional DNP3 communication stack.
1. Layered Integration
- DNP3 Secure Authentication (SA):
Provides encryption and message integrity using AES-256-GCM. It sits between the Application Layer and Transport Function, protecting all user data exchanged between masters and outstations. - Authorization Management Protocol (AMP):
Operates alongside the Secure Authentication function. AMP enforces role-based access control (RBAC) through centrally managed Access Control Lists (ACLs) and Routing Tables. These define which masters or users are permitted to issue specific operations. - Keys Repository:
Stores the cryptographic keys generated and updated through the LESS (Low-Entropy Shared Secret) onboarding process. Keys are used by both SA and AMP for secure session establishment, encryption, and authentication.
2. Communication Path
- External Protocols (solid lines):
Represent encrypted communication paths—such as master–outstation exchanges via serial, TCP/IP, or UDP/IP links.
Secure Authentication ensures confidentiality and integrity over these channels. - Internal Interfaces (dashed lines):
Show software-level interactions between AMP, ACLs, and SCADA database systems.
These internal links manage configuration, role definitions, and access policies.
3. Integration with SCADA Systems
At the top of the stack, the SCADA Application or Database interacts with the DNP3 Application Layer, which handles control logic, data points, and event reporting.
All sensitive operations (e.g., Select-Before-Operate, remote writes, or configuration updates) are authorized and validated through the Secure Authentication and AMP functions before execution.
4. Transport and Link Layer Foundation
The DNP3 Transport Function and Data Link Layer remain unchanged from earlier versions, ensuring full compatibility with existing DNP3 networks.
They handle segmentation, framing, and error checking—while the Serial and Internet Protocol Suite (TCP/UDP) layers provide physical and network connectivity.
This architecture demonstrates how DNP3 SAv6 transforms from a traditional open protocol into a layered security framework:
- AMP governs who can communicate and what they can do.
- Secure Authentication ensures how they communicate—safely, encrypted, and verifiable.
- The core DNP3 transport and link layers remain intact, preserving interoperability with legacy systems.
Key Design Simplifications
Compared with SAv5, Version 6 reduces complexity and attack surface by:
- Removing the multi-step Challenge/Reply sequence.
- Eliminating unused multi-user and “key-status request” features.
- Replacing random-challenge replay protection with AEAD nonces.
- Adding version identification during session startup for smoother interoperability.
- Supporting modern lightweight cryptographic primitives such as BLAKE2, SHA-3, and elliptic-curve algorithms for constrained devices.
The result is faster initialization, lower processing overhead, and easier implementation.
Core Enhancements in SAv6
1. Authenticated Encryption (AEAD AES-256-GCM)
SAv6 employs Authenticated Encryption with Associated Data (AEAD) using AES-256-GCM.
This single cryptographic process provides both confidentiality and integrity:
- Encrypts all DNP3 control and data payloads.
- Adds a cryptographic tag (MAC) to detect tampering.
- Uses unique nonces for replay prevention.
- Allows operation in authentication-only mode for diagnostic use.
This is the first DNP3 version offering full encryption at the protocol level.
2. Authorization Management Protocol (AMP)
AMP introduces centralized Role-Based Access Control (RBAC).
A trusted Authority—often part of a key management server—defines which users, masters, or systems are permitted to perform specific operations on each outstation.
Key functions:
- Centralized authorization and revocation.
- Role and privilege definitions (e.g., read-only, operate, maintenance).
- Audit and compliance logging.
- Optional Access Control Lists (ACLs) at the outstation for fine-grained control.
AMP shifts DNP3 security from device-level trust to system-level trust management, essential for large, distributed utilities.
3. Secure Device Enrollment (LESS Mechanism)
SAv6 introduces the Low-Entropy Shared Secret (LESS) process to simplify onboarding and key management.
- Each device stores a short shared secret (similar to a commissioning PIN).
- During enrollment, this secret bootstraps the creation of cryptographic keys.
- Subsequent Update Keys and Session Keys are generated automatically and wrapped using AES-Key-Wrap.
Benefits:
- No manual key transfer.
- Automatic rekeying and rotation.
- Lower human-error risk.
- Scalable for large multi-substation deployments.
Cryptographic Framework
| Key Type | Purpose | Algorithm / Use |
| Authority Key | Root key managed by AMP | RSA / ECC |
| Update Key | Protects new session keys | AES-256 Key Wrap |
| Session Key | Encrypts + authenticates messages | AES-256-GCM |
| LESS Secret | Onboarding bootstrap | Derived via AES / SHA |
Keys rotate periodically, ensuring Perfect Forward Secrecy (PFS) even if one session key is compromised.
DNP3 SAv6 Message Flow
- Master sends an encrypted, authenticated request using its session key.
- Outstation validates the GCM tag and checks AMP authorization.
- Authorized operations are executed; results are encrypted and returned.
- Nonces and timestamps ensure uniqueness and replay prevention.
This streamlined flow eliminates challenge–reply latency while maintaining end-to-end verification.
DNP3 SAv6 Enrollment and Authorization Process
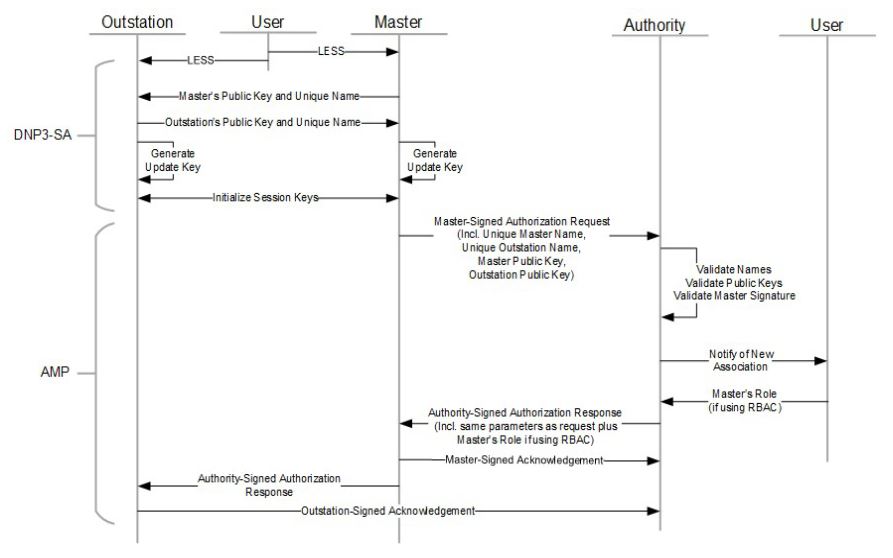
The figure above details the sequence of interactions that take place during the secure establishment of trust and communication between DNP3 devices.
1. LESS Key Exchange and Initialization
- Both the Master and Outstation begin by using the Low-Entropy Shared Secret (LESS) to bootstrap trust.
- Each side exchanges its public key and unique identifier (name).
- The shared secret is used to securely derive Update Keys, which in turn generate Session Keys for encryption and authentication.
Result:
The Master and Outstation now share unique session keys that will be used for AES-256-GCM–protected communication.
2. Authorization Request via AMP
Once the secure session is established, the Master sends an Authorization Request to the Authority.
This request includes:
- The Master’s unique name
- The Outstation’s unique name
- Both public keys
- A Master digital signature validating authenticity
The Authority verifies:
- The legitimacy of both identities
- The validity of the Master’s signature
- Any existing authorizations or revocations
3. Role Assignment and Authorization Response
If validation succeeds, the Authority issues an Authorization Response:
- Signed by the Authority’s private key
- Contains the same association parameters as the request
- Includes the Master’s role definition if RBAC (Role-Based Access Control) is used
The Master then sends a signed acknowledgment to confirm receipt and validity.
4. Outstation Acknowledgment and Finalization
- The Outstation receives and verifies the Authority-Signed Authorization Response.
- It then signs an Acknowledgment, completing the AMP authorization process.
- The result is a fully trusted, encrypted, and authorized communication link between the Master and Outstation.
Key Advantages of This Model
- Mutual authentication between all parties (Master, Outstation, Authority).
- Centralized role management—authorization handled by AMP.
- Secure onboarding using LESS—no manual key distribution.
- Cryptographically signed acknowledgments ensure end-to-end verification.
Backward Compatibility
At session start, DNP3 SAv6 devices exchange version identifiers:
- If both sides support SAv6 → full AEAD encryption and AMP enabled.
- If only SAv5 → fall back to authentication-only mode.
- If non-secure DNP3 → standard operation, no disruption.
Utilities can therefore upgrade gradually without interrupting legacy systems.
Deployment and Compliance
SAv6 aligns with modern regulatory frameworks including:
- NERC CIP-005, CIP-007, CIP-011
- IEC 62443-3-3
- DOE C2M2
Best Practices:
- Deploy a central Key Management Server for AMP and enrollment.
- Maintain time synchronization (NTP / PTP) for nonce validity.
- Rotate keys periodically and revoke unused roles.
- Segment or VPN-protect port 20000 (TCP/UDP) communications.
Advantages of SAv6 Over SAv5
| Feature | SAv5 (2012) | SAv6 (2020) |
| Encryption | None | AES-256-GCM (AEAD) |
| Authentication | HMAC-SHA-256 / AES-GMAC | Integrated GCM tag |
| Access Control | Basic User ID | Centralized RBAC via AMP |
| Key Management | Manual / semi-auto | Automated (LESS + AMP) |
| Enrollment | Manual setup | Secure auto-onboarding |
| Replay Protection | Random challenge | Nonce-based AEAD |
| Interoperability | SAv2–SAv5 | SAv2–SAv6 |
| Compliance Alignment | Limited | IEC 62443 & NERC CIP ready |
Conclusion
DNP3 Secure Authentication Version 6 delivers true end-to-end protection for modern SCADA networks.
By combining AES-256-GCM encryption, centralized authorization (AMP), and automated key management (LESS), it turns DNP3 into a resilient, cyber-secure framework capable of supporting decades of infrastructure growth.Utilities adopting SAv6 gain confidentiality, integrity, and accountability—all while maintaining interoperability with existing DNP3 systems.
For critical infrastructure security, IEEE 1815-2020 DNP3 SAv6 is the definitive standard moving forward.
