Modern critical infrastructure systems — such as electric utilities, water treatment, and oil & gas networks — rely heavily on SCADA communications to monitor and control field equipment.
One of the most trusted communication standards enabling this exchange is the Distributed Network Protocol version 3 (DNP3).
While DNP3 was originally designed for reliability and efficiency, its early versions offered no built-in protection against unauthorized access or message tampering. Recognizing this gap, the IEEE 1815-2012 standard formally introduced DNP3 Secure Authentication (DNP3-SA) — a framework that adds cryptographic protection and identity verification to the protocol without sacrificing interoperability or performance.
Table of Contents
What Is DNP3 Secure Authentication?
Defined in Clause 7 of IEEE 1815-2012, DNP3-SA provides a challenge–response security layer that verifies the identity of communicating devices and ensures that critical control commands originate from legitimate, authorized sources.
Rather than encrypting the data payload, DNP3-SA focuses on message authentication and integrity, confirming that every instruction or status message is genuine and unaltered.
The 2012 edition standardized Secure Authentication Version 5 (SAv5) — replacing older, less flexible models and establishing the foundation still used by most utilities today.
Objectives of DNP3 Secure Authentication
The IEEE 1815-2012 standard outlines several goals for Secure Authentication:
- Verify origin: Confirm that messages and control commands come from authorized masters or outstations.
- Ensure integrity: Detect any modification or corruption of transmitted data.
- Prevent replay attacks: Reject reused or duplicated messages.
- Support accountability: Associate every authenticated action with a user ID.
- Maintain interoperability: Allow secure and non-secure DNP3 devices to coexist on the same network.
How DNP3-SA Works
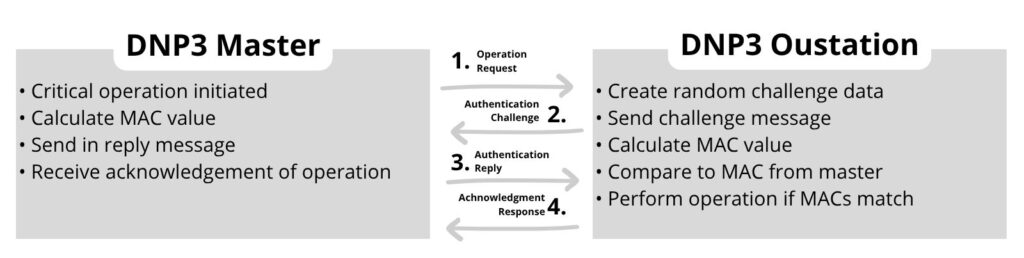
At its core, DNP3-SA adds a two-pass challenge–response process based on the ISO/IEC 9798-4 standard for message authentication codes (MACs). It operates entirely within the application layer of DNP3, leaving lower-level transport and link layers unchanged.
1. Challenge–Response Mechanism
When a master or outstation receives a command that requires authentication, it issues a challenge — a random number or token.
The sender then computes a MAC using that challenge and a shared session key, and sends the response.
If the receiving device computes the same MAC, it confirms the sender’s authenticity.
2. Aggressive Mode
To reduce network traffic, DNP3-SA defines an optional Aggressive Mode, where the sender includes its authentication information in the same message, avoiding a separate challenge exchange. This method balances efficiency with security and is widely used in modern devices.
3. Message Authentication Codes
MACs are cryptographic digests that verify message integrity. IEEE 1815-2012 allows algorithms such as HMAC-SHA-256 and AES-GMAC, ensuring strong protection against tampering and forgery.
Key Management and Cryptography
Secure Authentication depends on multiple keys that define trust relationships between communicating devices.
| Key Type | Purpose | Change Mechanism |
|---|---|---|
| Session Keys | Authenticate messages between master ↔ outstation | Updated periodically using Update Key |
| Update Key | Protects new session keys during changeover | Manually or by authority key |
| Authority Key (optional) | Enables centralized updates | Controlled by a trusted key authority |
AES-256 Key Wrap is the mandatory encryption method for key changes, while RSAES-OAEP-1024 and other asymmetric options are permitted for special cases.
Session keys are rotated periodically to achieve perfect forward secrecy, ensuring that a single compromise does not expose past communication.
Authentication Objects (Group 120)
IEEE 1815-2012 defines a dedicated set of DNP3 objects for Secure Authentication, grouped under Object Group 120.
These objects carry authentication requests, replies, key updates, and error codes within standard DNP3 frames.
| Object Variation | Description |
|---|---|
| g120v1 | Challenge |
| g120v2 | Reply |
| g120v3 | Aggressive Mode Request |
| g120v4–v5 | Session Key Status and Request |
| g120v7 | Error Message |
| g120v13–v15 | Update Key Change, Confirmation, and Signature |
This structure allows seamless integration of authentication data into existing DNP3 messaging without altering the underlying communication model.
Multi-User Support and Auditing
DNP3-SA introduces multi-user capability, where each user or system component has a unique identifier and associated keys.
This enables individual accountability for operations such as remote switching, set-point adjustments, or parameter updates — a key requirement for regulatory compliance (e.g., NERC CIP).
Audit logs can record:
- Which user authenticated a specific command,
- When it was sent, and
- Whether authentication succeeded or failed.
Interoperability and Backward Compatibility
A major advantage of DNP3-SA (SAv5) is its backward tolerance. Devices that support authentication can communicate securely when possible, yet still interact with non-secure devices if required.
The protocol defines configuration options to enable or disable authentication per association, ensuring gradual rollout in large networks.
Security Algorithms and Defaults
IEEE 1815-2012 lists approved algorithm suites for key management and authentication.
The default method uses AES-256 Key Wrap for secure key exchange and HMAC-SHA-256 for message authentication.
Optional alternatives include AES-GMAC or asymmetric RSA/DSA methods for special applications.
This flexibility allows implementers to choose algorithms that meet both security requirements and device resource limits.
Error Handling and Recovery
If an authentication attempt fails — for example, due to mismatched MACs or expired keys — the receiving device must reject the operation.
To prevent denial-of-service attacks, the standard limits the number of error responses and defines clear state machines for resynchronizing session keys and challenges.
Advantages of DNP3 Secure Authentication
| Benefit | Description |
|---|---|
| Strong message integrity | Every critical message is verified cryptographically. |
| Defense against spoofing | Prevents impersonation of control devices. |
| Replay protection | Sequence numbers stop reuse of old messages. |
| Granular user control | Multi-user and role-based permissions. |
| Low overhead | Authentication only, no full encryption required. |
| Backward compatibility | Works alongside non-secure DNP3 devices. |
These capabilities give operators confidence that control signals and event data come from trusted sources — vital for safety-critical networks.
Practical Implementation Considerations
To deploy DNP3-SA effectively:
- Upgrade firmware on RTUs, IEDs, and masters to IEEE 1815-2012-compliant versions.
- Distribute initial Update Keys securely (e.g., via secure USB or offline means).
- Schedule periodic key changes based on policy.
- Monitor authentication logs to detect repeated failures or anomalies.
- Use secure networks (VPNs or private links) to add defense-in-depth.
Even though DNP3-SA does not encrypt data, it drastically reduces the likelihood of unauthorized control actions or data manipulation.
From Version 5 to Version 6 and Beyond
The security model in IEEE 1815-2012 laid the groundwork for later enhancements.
DNP3 Security Version 6 (2020) built upon these principles, introducing optional encryption, simplified key enrollment, and centralized Authorization Management Protocol (AMP).
Still, the Version 5 model defined in 2012 remains the global baseline for secure, authenticated SCADA communication.
Conclusion
The inclusion of DNP3 Secure Authentication in IEEE 1815-2012 was a turning point for industrial cybersecurity.
It transformed DNP3 from a reliable yet exposed protocol into one capable of verifying every command and message that passes through a SCADA network.
By implementing DNP3-SA, utilities and industrial operators gain a cost-effective way to protect their assets, improve accountability, and comply with evolving security standards — all while maintaining compatibility with existing infrastructure.
