In power automation, reliable and secure data exchange between control centers and field devices is critical. One of the most adopted communication protocols that enables this is Distributed Network Protocol version 3 (DNP3).
DNP3 communicates over TCP/UDP port 20000, which serves as the standard IP port for linking SCADA master stations with remote field units like RTUs and IEDs.
This article explores everything you need to know about the DNP3 port, its configuration, functions, security, and best practices for safe deployment in power automation systems.
What Is the DNP3 Port?
The DNP3 port is the default network port assigned to DNP3 communications when operating over TCP/IP or UDP/IP. The Internet Assigned Numbers Authority (IANA) officially reserves port 20000 for DNP3 traffic, ensuring interoperability across different vendors and systems.
| Protocol | Transport | Port | Description |
|---|---|---|---|
| DNP3 | TCP | 20000 | Reliable, connection-oriented communication |
| DNP3 | UDP | 20000 | Lightweight, connectionless communication (less common) |
When devices communicate using DNP3 over IP networks, both the master and the outstation use this port to establish or listen for incoming connections. Having a standardized port number simplifies configuration and ensures that SCADA devices from different manufacturers can communicate seamlessly.
TCP vs. UDP in DNP3 Communication
When the DNP3 protocol operates over IP networks, it relies on transport layer protocols to handle data transmission — primarily Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). Both play an important role, but they work in very different ways.
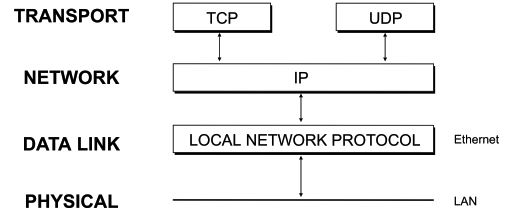
DNP3 can run over both Transmission Control Protocol (TCP) and User Datagram Protocol (UDP).
Transmission Control Protocol (TCP)
Transmission Control Protocol (TCP) provides a reliable, connection-oriented method for transferring data between two devices on a network. It operates on top of the Internet Protocol (IP), using IP to deliver datagrams while ensuring that data arrives error-free at the destination TCP layer.
TCP establishes communication links between “sockets” on each end of the connection. Once the link is initialized, data can flow in both directions simultaneously. The protocol divides data into segments, which are then passed down to IP. IP may further break these segments into smaller datagrams for transmission across the network.
Each TCP segment includes a header that is typically between 20 and 24 bytes long. The segment size is based on the maximum segment size (MSS) negotiated between both ends of the connection — or defaults to 536 bytes when communicating with a non-local IP address.
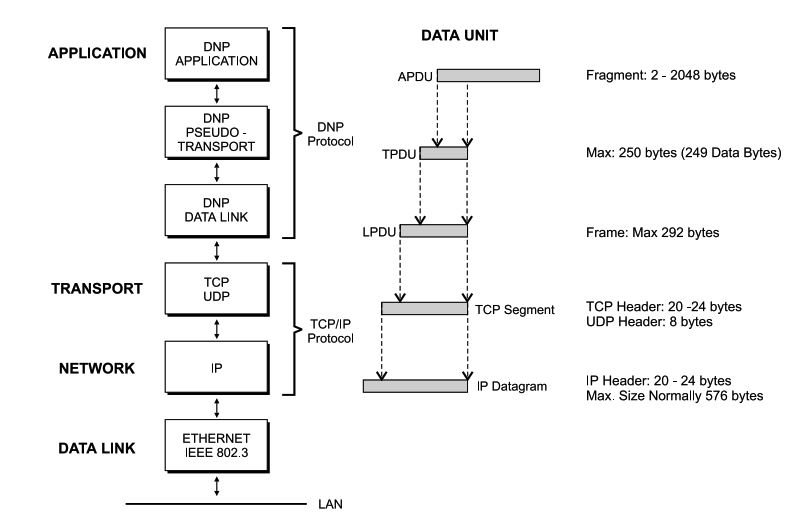
User Datagram Protocol (UDP)
User Datagram Protocol (UDP) provides a simple way for applications to access the datagram service offered by the Internet Protocol (IP) directly from the transport layer. Each UDP datagram corresponds to a single IP datagram, containing additional information such as the source and destination ports and a checksum for basic error detection.
Unlike TCP, UDP does not include mechanisms for reliable delivery. If a transmission error is detected, the affected packet is simply discarded. Since UDP is connectionless and packet-based, it does not establish a dedicated session between devices.
This lightweight, stateless design allows UDP to support broadcast and multicast communication, enabling data to be sent to multiple destinations at once—ideal for applications that prioritize speed and efficiency over guaranteed delivery.
Example: Capturing DNP3 Traffic on Port 20000
The screenshot below shows a Wireshark capture of DNP3 messages being exchanged over the dnp3 default TCP port 20000 on a local loopback interface (127.0.0.1). This example illustrates how DNP3 traffic appears when inspected at the packet level.
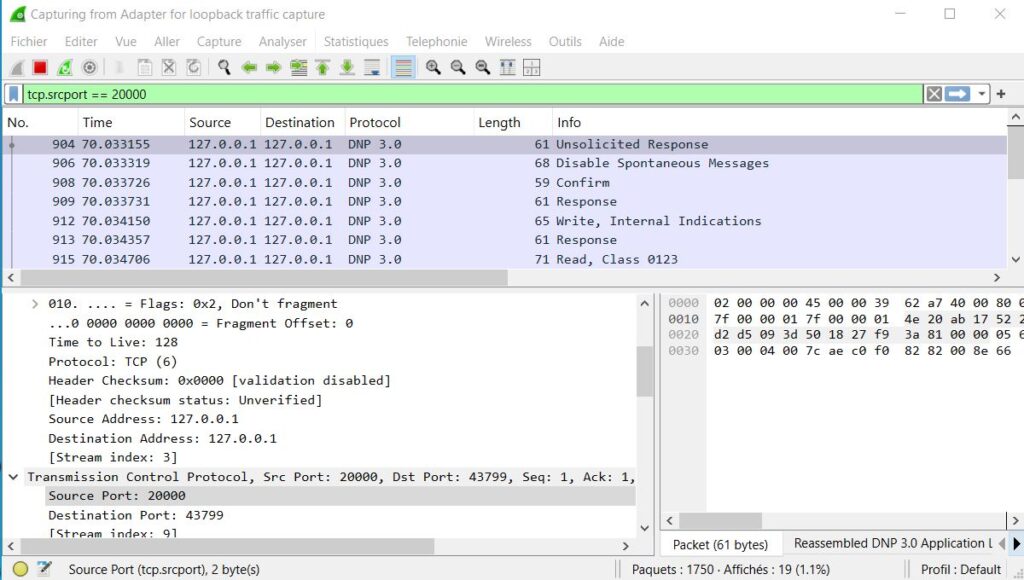
In this capture:
- The filter
tcp.srcport == 20000was used to display packets where DNP3 is the source communication port. - Communication occurs between the local host (
127.0.0.1) as both source and destination, which is typical for a loopback test. - The Protocol column identifies the traffic as DNP 3.0, confirming that DNP3 is running over TCP/IP.
- The Info column lists message types such as:
- Unsolicited Response
- Confirm
- Write, Internal Indications
- Read, Class 0123
In the lower Wireshark pane, the Transmission Control Protocol section shows that:
- The source port is 20000, the standard port for DNP3 over TCP/IP.
- The destination port (in this example, 43799) is dynamically assigned by the receiving device.
- The protocol field is set to TCP (6), indicating reliable, connection-based communication.
This confirms that DNP3 messages are being properly transmitted over TCP using port 20000 — exactly as defined by the DNP3 standard. Wireshark is an excellent tool for verifying connectivity, diagnosing communication errors, or confirming port configuration in a SCADA test environment.
Configuring the DNP3 Port
In most SCADA environments, port 20000 is configured automatically, but engineers can modify it when custom networking rules or security constraints apply.
Typical Configuration Steps
- Access the communication settings of the SCADA master or RTU.
- Verify that the TCP/UDP port 20000 is assigned for DNP3.
- Ensure firewalls allow inbound and outbound traffic on port 20000.
- Test communication between the master and field devices.
Network tools such as Wireshark can be used to capture and analyze DNP3 packets. Applying the filter tcp.port == 20000 quickly isolates DNP3 traffic for troubleshooting.
DNP3 Port Security
Because port 20000 is a well-known and globally registered port, it is a common target for network reconnaissance and potential cyberattacks. Therefore, securing DNP3 communication is a crucial step in industrial cybersecurity.
Recommended Security Measures
- Firewall Configuration:
Only permit port 20000 traffic between trusted network zones (control center and substations). - Network Segmentation:
Isolate SCADA systems from corporate or public networks using VLANs or DMZs. - VPN Tunnels:
Use encrypted VPNs for remote access to DNP3 devices. - DNP3 Secure Authentication (DNP3-SA):
Implement authentication mechanisms to verify both parties before communication. - Regular Monitoring:
Deploy intrusion detection systems (IDS/IPS) to monitor activity on port 20000.
DNP3 Secure Authentication (DNP3-SA)
To enhance security, the DNP3 Secure Authentication (SA) standard adds a cryptographic layer to standard DNP3 communication.
It introduces:
- Challenge-response authentication to prevent impersonation.
- Role-based access control for users and devices.
- Integrity protection to detect message tampering.
By enabling DNP3-SA, even if attackers can reach port 20000, they cannot execute unauthorized commands or extract data.
Comparison with Other Industrial Protocol Ports
| Protocol | Default Port | Transport | Application Area |
|---|---|---|---|
| DNP3 | 20000 | TCP/UDP | SCADA communication for utilities |
| Modbus TCP | 502 | TCP | Industrial automation |
| IEC 60870-5-104 | 2404 | TCP | Power transmission systems |
| OPC UA | 4840 | TCP | Data integration and IoT connectivity |
This comparison highlights how DNP3’s use of port 20000 distinguishes it as a highly reliable and standardized protocol for mission-critical control networks.
Conclusion
Port 20000 is far more than a simple network endpoint — it is the gateway through which DNP3 enables real-time industrial control. By understanding its role, securing its configuration, and following best practices, engineers can ensure that their SCADA systems remain both reliable and resilient against evolving cyber threats.
In short, the DNP3 port (20000) is the foundation of secure, standardized communication in modern energy, water, and utility networks — a small number that plays a massive role in industrial reliability.

Si zakaria,
Ces vraiment très intéressant un grand merci pour votre effort a élaboré ce site très riche en information concernant les protocols de communication bonne chance pour la suite…..